AMABHUNGANE: SANITISER SCAM, PART 1
Gone phishing: Business owner almost scammed by fake Covid-19 tender

Fraudsters claiming to be health department officials are peddling tenders for a non-existent sanitiser machine.
See accompanying article: Phishing: Impersonating officials and what to do about it , and Part 2 ,Wild West Web: the return of the scam.
Bogus government tenders appear to be targeted at businesses listed on the national Treasury’s Central Supplier Database (CSD) because of a suspected leak within the publicly inaccessible database.
This database is, as it claims, a “single source of key supplier information” for organs of state. Businesses register on the CSD and can then be considered for government contracts.
One business owner, who spoke to amaBhungane on condition of anonymity, explained that she only began to receive these bogus tenders when she applied to list her company on the database. She also fell for one such tender.
On 8 April 2020, the Department of Health sent out an email to businesses about a new tender for industrial sanitiser machines – specifically, for the DX610M model.
Prospective suppliers had six days to respond to the bid, which closed on 14 April.
Typically, when responding to a tender, there should be sufficient generic information accompanying the description of the tender, so that individual businesses can meet almost all the requirements with their own products – in this case, a sanitiser machine.
The business owner did a cursory investigation and concluded that the request for quotation (RFQ) seemed legitimate. She then responded to the request.
One day after submitting her bid, the business owner received a call from a supply chain official, Tshepo Mokoena. He congratulated her on her successful bid application.
Mokoena then asked her for the batch number on the product to check whether it would meet the requirements of the South African Bureau of Standards. “This seemed weird,” the business owner said – because a batch number is only given after a product is manufactured.
He then asked her if she was sourcing the sanitiser machines locally, explaining that she had a 90% chance of losing out on the bid if she did not do so. He promised to provide her with a list of local producers.
In the end, he sent her the name and contact numbers of one company: Sanetex Hygiene.
Sanetex Hygiene also appeared to be the only company, after a cursory Google search, that could source the specific DX610M sanitiser machine for R7 500 per unit.
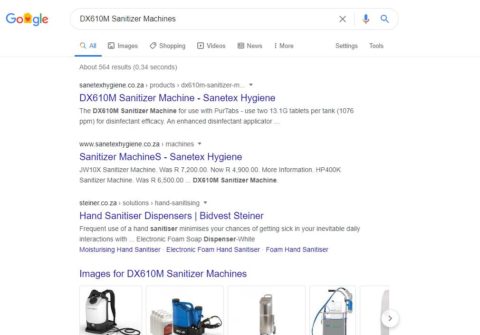
To secure her bid, the business owner planned to order the machines from Sanetex Hygiene to supply the Department of Health. However, she was alarmed when she received a response from the Russian equivalent of a Gmail address – an unusual email account for a South African business.
When Mokoena called the business owner the next day, she asked him about the Yandex email address. He hung up on her.
Had the business owner followed through with the tender, she would have paid for non-existent machines for a non-existent tender from a fake Department of Health official.
Several business owners say they have received RFQs for products ranging from geysers and wheelchairs to the electric cables required for trains used by the Passenger Rail Agency of South Africa (Prasa). Such requests might have been appropriate if the businesses specialised in these products.
Advocate Jacqueline Fick, a forensic investigator specialising in electronic fraud, told amaBhungane that because of the large ecosystem of departments connected to the database to verify suppliers’ credentials, there were vulnerabilities in the system. This ecosystem includes the Department of Home Affairs, the South African Revenue Service, company registrations that appear on the database of the Companies and Intellectual Property Commission, and government employees on the public service payroll system known as Persal.
Maria Pienaar, principal at Pienaar Consulting and formerly the chief information officer at Cell C, said: “When departments in organisations are disjointed, it creates opportunities for fraud. In the case of government departments, each government department is responsible for their own budgets and how they apply these standards in the systems they implement.
“This leaves gaps for cyber fraud if there are not appropriate governance measures and audits in place to ensure compliance or if budgets are not appropriately applied to alleviate these risks.”
When asked for comment, national Treasury said: “The system was checked and proofed against phishing and hacking before the volatile situation of Covid-19. This is done frequently to ensure that possible breaches are prevented.”
According to the Treasury, there are more than 500,000 listed suppliers on the website and more than 700,000 registered users. More than 800 government departments and state-owned enterprises use the database to identify suppliers and check for compliance.
With the marked decrease in face-to-face human interaction as a result of the outbreak of the coronavirus pandemic, the opportunity for fraudsters to take advantage of business owners will rise exponentially.
So, what had the business owner missed?
This bid had several dodgy elements to it: the urgency of the bid; the short time-frame that businesses had to respond to it; the monopoly of suppliers for the item; and the unusual government email address: healthsupplychain-za.org.
When amaBhungane called the number listed on the email for comment and explained our intentions, the operator dropped the call.
According to the CSD website, fraudsters “send a fictitious RFQ from what would seem to be a governmental email address and use a fake RFQ form with a logo and contact details of the contact person. These requests are usually ‘urgent’ and the whole process is concluded within a short period of time.”
In 2016, the department of health complained of a high number of scammers using the following emails:
- @gautenghealth-gov.org.za
- treasury-gov.org.za
- [email protected]
- mphumalang-gov.org.za
- NDOH@nationalhealth
- @dh.gov.co.za
- org.za
- [email protected]
- [email protected]
The official national department of health’s emails end with “@health.gov.za”.
To top it all, Sanetex Hygiene was not registered with the companies’ registrar and its website was created a day before lockdown was implemented. When amaBhungane phoned the business to ask about its company registration, the operator dropped the call.
Sanetex Hygiene’s website has since been taken down after the businesswoman reported it to its domain registry, but you can see a cached version of it here, and a screenshot of the website here.
In August last year, the Treasury advertised a tender for the maintenance of the database and awarded the contract to local IT firm Gijima for three years, starting from 1 April 2020. The contract is valued at over R42 million.
According to the tender document, Gijima will not only be expected to manage the database and prevent the duplication of suppliers, but in terms of cyber security, it will also be required to implement standardised electronic verification of supplier information to reduce fraud.
In the meantime, the Treasury has said that the key to avoid being scammed is for businesses to “reduce the number of sectors and commodities they register for, so that they recall these when the scam RFQ reaches them, that they are not registered for this particular item or commodity.
“[Businesses need to] make sure they do not deviate from the services or commodities they registered for on the CSD, as most [business owners] who fall for scams do.
“[They need to] be familiar with the institutions they do business with, and their mandates, amongst others. [They need to] protect their company information when sharing in what they refer to [as] ‘networking sessions’.” DM
The amaBhungane Centre for Investigative Journalism, an independent non-profit, produced this story. Like it? Be an amaB Supporter to help us do more. Sign up for our newsletter to get more.

















 Become an Insider
Become an Insider